Fortinet Discreetly Patches CVE-2023-27997, a Known Exploited Vulnerability
According to Fortinet, 110 vulnerabilities affecting Fortinet software were announced since the beginning of 2023. On June 8th, security fixes were released in FortiOS firmware versions 6.0.17, 6.2.15, 6.4.13, 7.0.12, and 7.2.5. Interestingly, no specific reference to a CVE patch was provided, raising questions about the nature and extent of the new version release’s purpose.
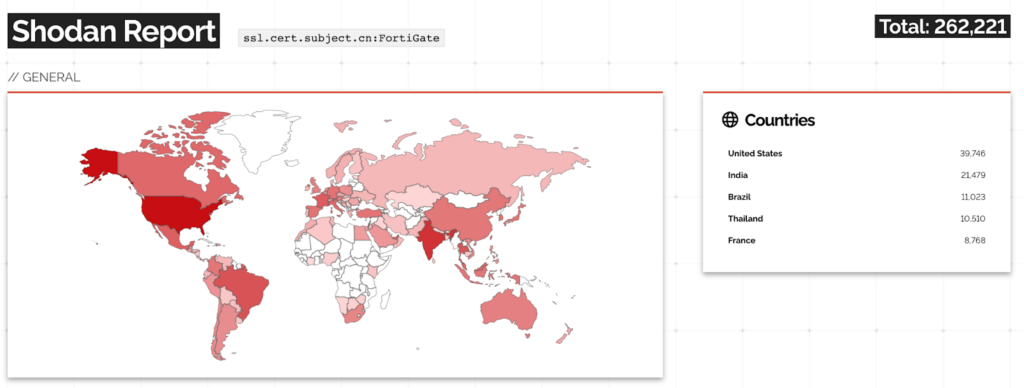
In a surprising turn of events, Fortinet published 21 new CVEs on June 12th. These disclosures appear to be connected to the significant patch implemented on June 9th which Fortinet kept discreetly. Among the recent CVEs, one specific vulnerability demands immediate attention, CVE-2023-27997, which is known to be exploited in the wild, and joins the concerning list of 11 Fortinet vulnerabilities that are already known to be exploited in the wild, as reported by CISA KEV. The number of Fortinet instances exposed to the internet, as determined by a Shodan search, currently stands at a significant 648,983.
June 12th Published CVEs
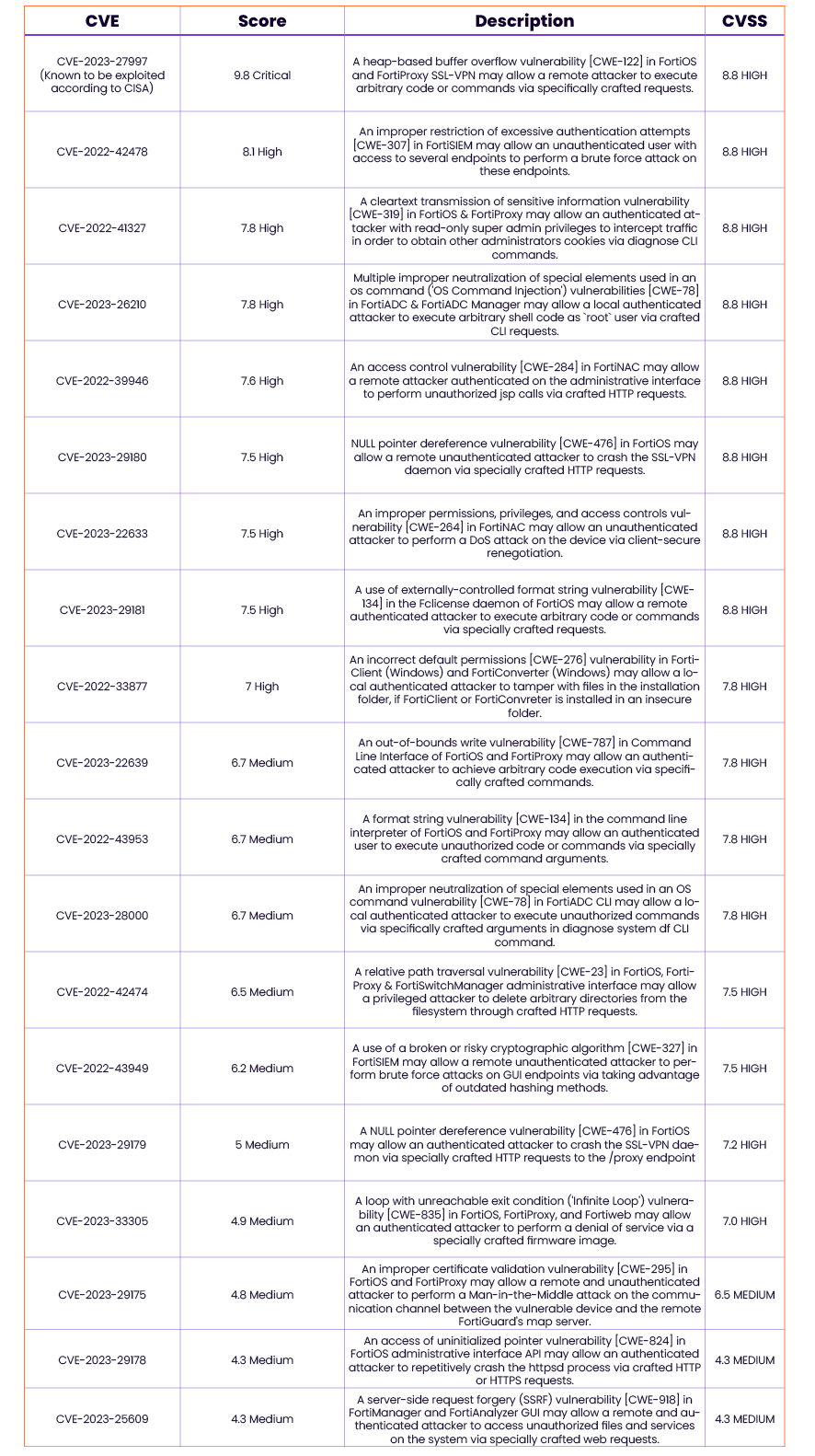
The following table provides a breakdown of the 21 CVEs patched by Fortinet.
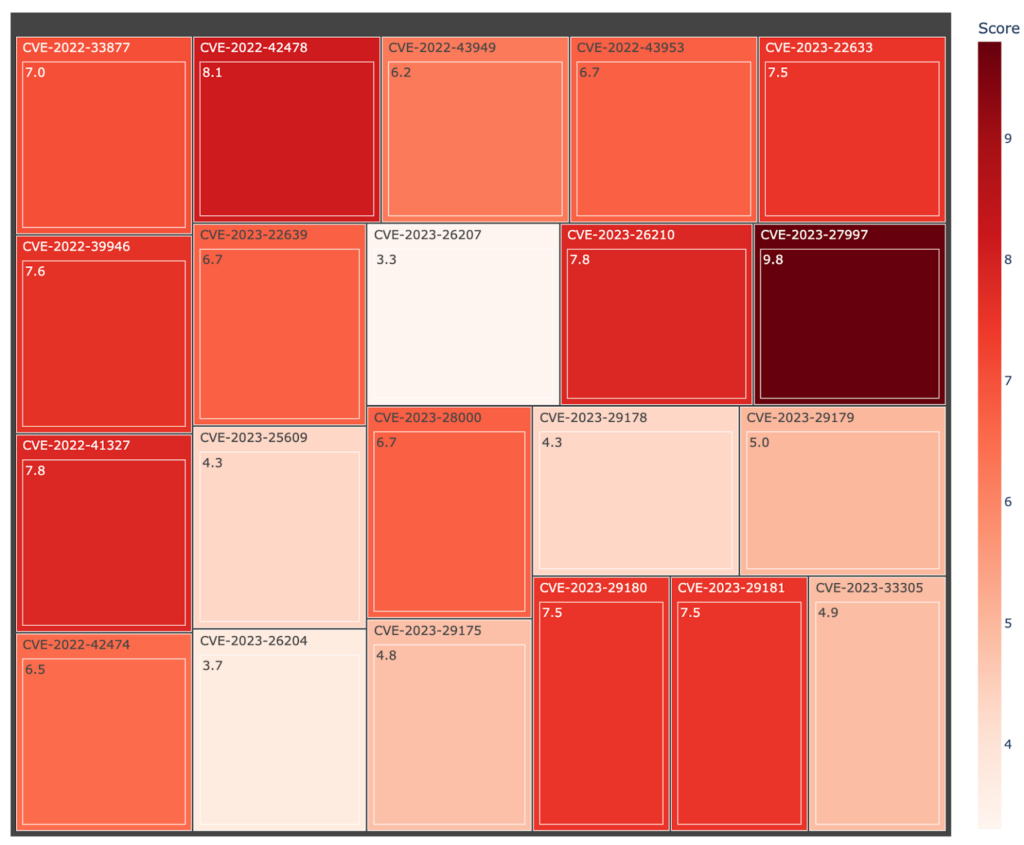
The following treemap portrays the 22 CVEs patched on the June 12th release, along with their CVSS score. The darker the color, the higher the score.
CVE-2023-27997: Pre-authentication Remote Code Execution on Fortigate VPN
CVE-2023-27997 is a 9.8 Critical Heap Overflow vulnerability that can lead to Remote Code Execution in FortiGate SSL-VPN. The vulnerability was found in the internet-facing interface VPN and targets governments, manufacturers, and critical infrastructure. The vulnerability was found by Charles Fol and Dany Bach who also published detailed information about the flaw and the exploit.
SSL-VPN
VPN (Virtual Private Network) is a service that facilitates a secure and encrypted connection between a user on the public internet and an organization’s private network. It ensures that data transmitted between the user and the network remains protected from potential eavesdropping and unauthorized access.
SSL-VPN (Secure Socket Layer Virtual Private Network) is a specific type of VPN technology that allows users to securely access an organization’s network resources without the need for additional software installations. It leverages the SSL protocol or its successor, TLS (Transport Layer Security), to establish a secure and encrypted connection.
Exploit
The bug can be triggered by sending HTTP GET/POST requests to any of the two URLS: /remote/hostcheck_validate, and /remote/logincheck via a parameter named enc. This parameter contains encrypted data, including a seed, size, and ciphertext. The seed is used to compute an XOR keystream, which is then used to decrypt the data.
There are two flaws in the decryption process, however. First, the comparison of the payload length is incorrect, comparing only the lower-significance byte of the given length. Second, the payload length is represented in hexadecimal, while the actual length is in raw bytes, leading to potential size miscalculations.
By exploiting these flaws, an attacker can allocate a chunk of arbitrary size and XOR bytes beyond the buffer with a keystream of MD5 hashes. The exploitation process involves triggering the bug multiple times to achieve specific memory modifications. By controlling the keystream and manipulating the length parameter, the attacker can set arbitrary values in memory and overwrite specific bytes.
Recommendations
Remediation
Upgrade FortiOS and FortiProxy to the latest versions released:
- Upgrade to FortiOS-6K7K version 7.0.12 or above
- Upgrade to FortiOS-6K7K version 6.4.13 or above
- Upgrade to FortiOS-6K7K version 6.2.15 or above
- Upgrade to FortiOS-6K7K version 6.0.17 or above
- Upgrade to FortiProxy version 7.2.4 or above
- Upgrade to FortiProxy version 7.0.10 or above
- Upgrade to FortiOS version 7.4.0 or above
- Upgrade to FortiOS version 7.2.5 or above
- Upgrade to FortiOS version 7.0.12 or above
- Upgrade to FortiOS version 6.4.13 or above
- Upgrade to FortiOS version 6.2.14 or above
- Upgrade to FortiOS version 6.0.17 or above
Mitigation
If the patch cannot be applied, it is recommended to disable the SSL-VPN service.
Conclusion
The increasing number of vulnerabilities discovered in Fortinet software highlights the ongoing battle against cyber threats and raises concerns about the overall security assessment of Fortinet.
The disclosure of numerous CVEs and the discreet patching of CVE-2023-27997, a critical vulnerability exploited in the wild, emphasize the need for individuals and organizations to prioritize proactive security measures. This includes adopting platforms with a strong vulnerability management framework, promptly applying software updates, and implementing robust security practices. By doing so, users can enhance their defenses and mitigate potential risks associated with these vulnerabilities. It is crucial to stay vigilant and proactive in safeguarding against exploits that could compromise sensitive information and critical infrastructures.
The post Fortinet Discreetly Patches CVE-2023-27997, a Known Exploited Vulnerability appeared first on Rezilion.
*** This is a Security Bloggers Network syndicated blog from Rezilion authored by Yotam Perkal. Read the original post at: https://www.rezilion.com/blog/fortinet-discreetly-patches-cve-2023-27997-a-known-exploited-vulnerability/