The Ultimate Guide to Enterprise Risk Management Strategy

Enterprise risk management is a nebulous, hard-to-define topic area. It encompasses a large variety of risks and procedures for the enterprise and it differs greatly from traditional risk management.
So, what exactly is enterprise risk management? In this article, we’ll establish what it is, present two common enterprise risk management strategies, and emphasize the value of having enterprise-ready software to help simplify the process.
What is enterprise risk management?

According to the Committee of Sponsoring Organizations of the Treadway Commission (COSO), enterprise risk management is defined as “the culture, capabilities, and practices, integrated with strategy-setting and its performance, that organizations rely on to manage risk in creating, preserving, and realizing value.”
Put simply, enterprise risk management is the monitoring and remediation of the all-encompassing risks a business enterprise faces. These include all areas of risk management and are not limited to just cyber and info security. The key difference is that enterprise risk management is not siloed into different risk areas; it concerns all of them from one holistic view.
The 8 Types of Enterprise Risk
There are eight common types of enterprise risks to consider when learning about enterprise risk management, each of which are outlined below:
1. Financial Risk
One of the most common enterprise risks — financial risk — can affect the company’s overall financial standing, with one such example being debt. If a company takes on too much debt, it could affect operations and potentially halt business procedures. For this reason, it is one of many types of financial risk an enterprise may face.
2. Operational Risk
Operational risk is any risk that can affect the day-to-day operations of the company. Some examples include a wifi outage in the office, a telecommunications failure during meetings, or even supply chain disruptions. All of these risks — and more — can affect the operations of an enterprise, resulting in a loss of capital.
3. Strategic Risk
Strategic risks can impact the future plans of the company. Examples include the loss of a strategy to a competitor, being undercut in pricing, or market disruption by competitors. Anything affecting the strategy and future of the enterprise can be considered a strategic risk.
4. Compliance Risk
One of the most essential components to enterprise risk management, compliance risk is any compliance and rules and regulations the company must follow. This could be anything from accounting procedures to following certain standards in the industry, such as risk management frameworks. By monitoring controls in these compliance areas, enterprise companies can prevent compliance risk from affecting business operations.
5. Economic Risk
Economic risk concerns the global economy and financial markets. If an enterprise is public, shareholders hold it to certain standards. Any major disruptions in the global economy may impact the financial markets, resulting in an unstable stock market. This can affect the enterprise by causing investors to sell and result in a company losing capital.
6. Legal Risk
Legal risk encompasses the fact that an enterprise may be sued by a customer or third-party at any time. Lawsuits are time- and resource-consuming, and the public details of a legal matter can also cause disruptions to business operations. Customers may boycott the company or there may be large fines involved with the lawsuit, which will affect the enterprise.
7. Natural Disasters
Earthquakes, tornadoes, hurricanes, tsunamis, and more are all considered enterprise risk. Natural disasters can disrupt manufacturing if a plant is damaged or workers are affected by the disaster. It can also impact the workforce if they live in an area prone to natural disasters.
8. Security Risk
Lastly, enterprise risk management must take security risk into account. Security risk typically consists of a malicious threat actor taking action against the company in some way. This might be through a cyber attack, such as phishing, an issue with the physical security of a site, a data breach of sensitive client information, or even theft of physical items in a retail store.
The 8 Components of Enterprise Risk Management
Enterprise risk management differs from traditional risk management in that it has more components. You might be familiar with the four pillars of risk management, but if not, they include risk identification, risk evaluation, risk handling, and risk controlling. They are just part of what constitutes enterprise risk management. Using the COSO framework for enterprise risk management, we can actually identify eight components: internal environment, objective setting, event identification, risk assessment, risk response, control activities, information and communication, and monitoring. Let’s discuss each in detail and how they work together.
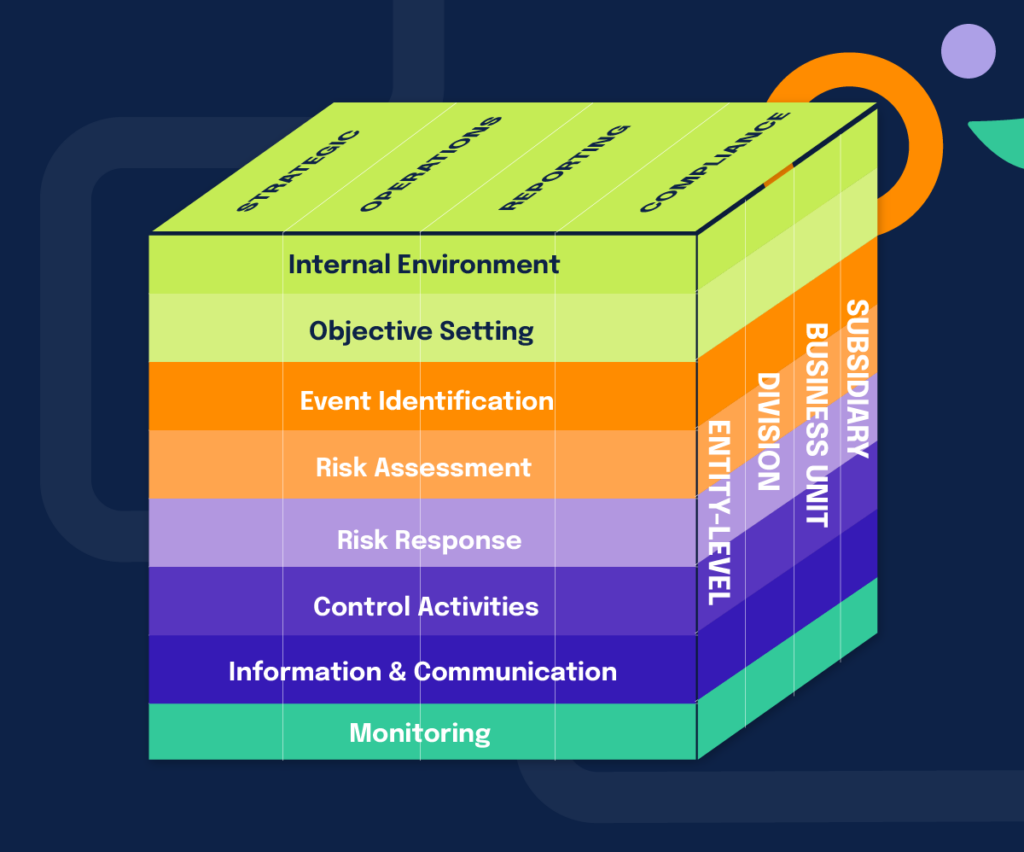
1. Internal Environment
The internal environment of an enterprise is essential to enterprise risk management. How risk is perceived and remediated must be established by leadership, as well as the risks they face and the organization’s overall risk appetite.
2. Objective Setting
Enterprises must set objectives before they can measure risk. These objectives must also align with the organization’s risk appetite, as well as their mission.
3. Event Identification
Any events — both internal and external — that may impact the enterprise have to be identified. They can be categorized in two ways: as risks to the organization or as opportunities for the organization.
4. Risk Assessment
Once risks have been identified, they can be assessed and tied back to the business’ objectives. This allows the organization to track them. Likelihood and impact should be assessed on a regular basis. Assessment should occur regularly and at all levels of the enterprise.
5. Risk Response
Responding to risks can take many forms in enterprise risk management. Typically it will occur in four ways: avoiding the risk, accepting the risk, reducing the risk, or sharing the risk. Decisions are made based on the risk tolerance and risk appetite of the enterprise.
6. Control Activities
Once risk response has been determined, it is time to execute and monitor the risks and their related activities. These are set up as controls so the enterprise can track and make progress toward its ideal risk posture.
7. Information and Communication
To remediate risk, employees need to understand what is being asked of them. Determining what is relevant to which stakeholders across the enterprise is a difficult task, but it must be done in order to identify, assess, and respond to risks.
8. Monitoring
For enterprise risk management to be successful, it must be monitored at all levels. This allows for the organization to be able to respond dynamically at any time to changes in its environment and risks.
Enterprise Risk Management Strategy: Two Effective Approaches
Three Lines Model
Developed by the Institute of Internal Auditors (IIA), the Three Lines Model “helps organizations identify structures and processes that best assist the achievement of objectives and facilitate strong governance and risk management.”
It is a strategy for managing risk, often implemented at the enterprise level, but it applies to all risk management. In the Three Lines Model, there are four entities: the governing body, management, internal auditors, and external assurance providers. Within the management and internal audit entities are the three lines for which the model is named.
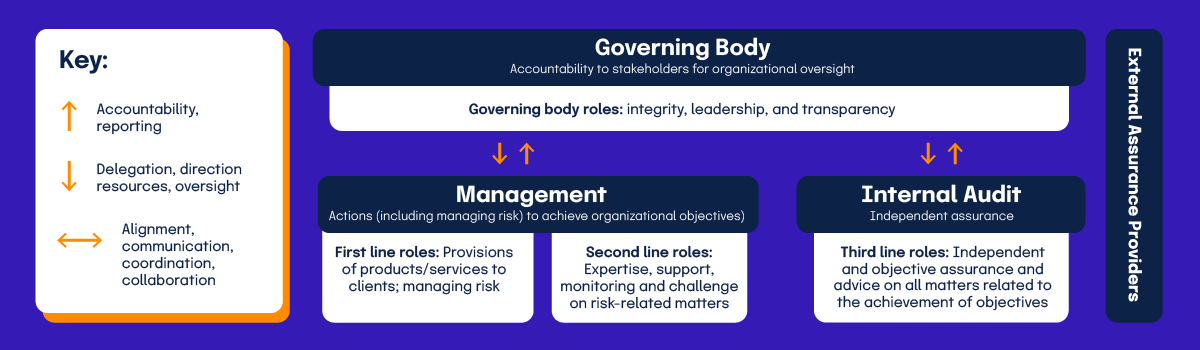
First and Second Line
Per the IIA, first line roles “are most directly aligned with the delivery of products and/or services to clients of the organization, and include the roles of support functions.” Meanwhile, second line roles “provide assistance with managing risk.” These lines are the first two layers of defense for the company against risk. Their roles both impact a company’s risk as they go about achieving organizational objectives. As risk managers and stakeholders with more expertise, these lines are essential to the overall enterprise risk management. Both report to the governing body but also receive oversight from it.
Third Line
The third line is internal audit, which “provides independent and objective assurance and advice on the adequacy and effectiveness of governance and risk management.” Independence from management is essential to ensure that the entity remains objective and free from bias. They do, however, have accountability to the overall governing body and oversight from it.
External Assurance Providers
The external assurance providers “complement internal sources of assurance,” so that there is an added layer of objectivity. They do not have shared objectives like the other entities, and therefore can provide a truly neutral perspective to the risk management activities.
Action-Oriented Matrix
DLA Piper has developed an action-oriented matrix that divides risk into four categories: improve, monitor, tolerate, and operate. This matrix helps organizations allocate resources, budget, and staff to the risks that need the most attention. Risks falling in the “Tolerate” and “Operate” categories require less attention than those in the “Improve” and “Monitor” categories.
Risks in the “Improve” category should be the primary focus of the organization, but stakeholders should continue to track and monitor risks in the “Monitor” category to ensure that they do not become more severe.
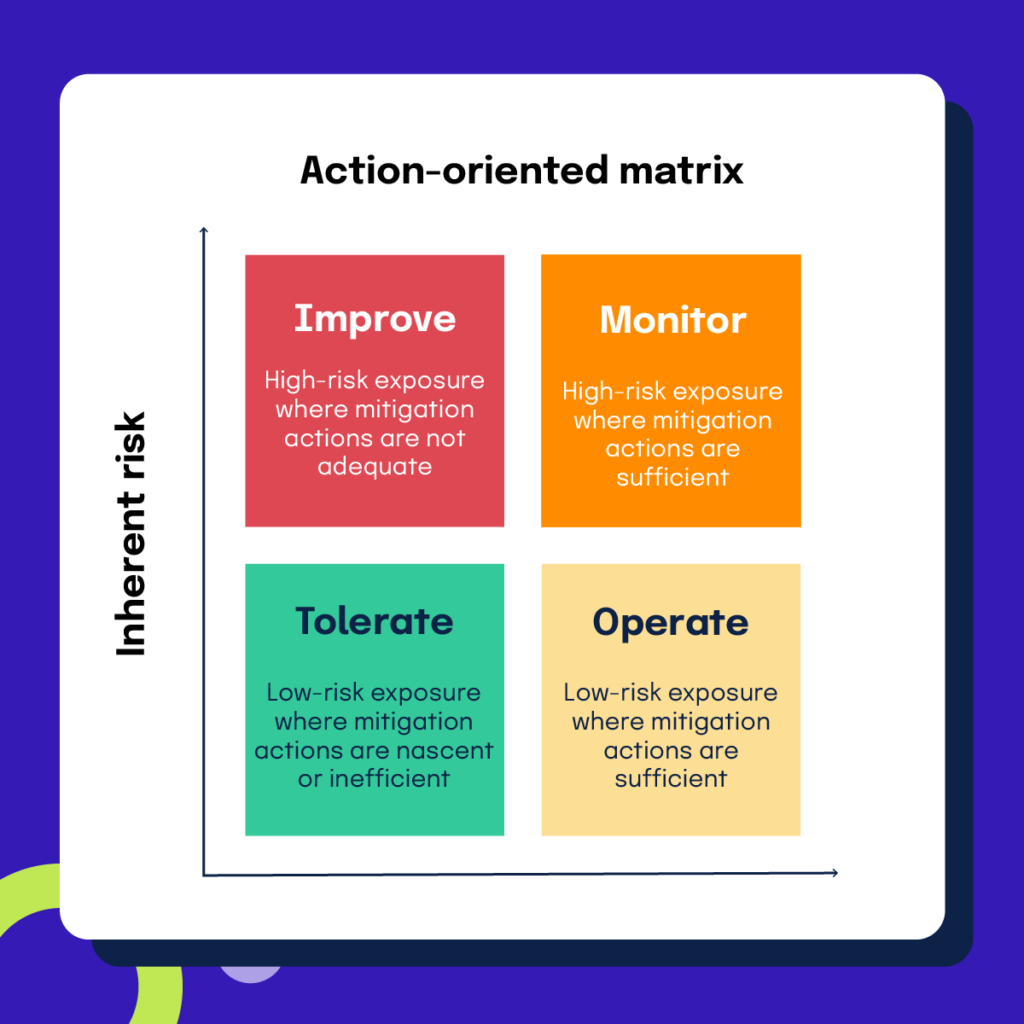
Functional groups and individuals should remain aware of all four of the categories, whereas management groups should only be concerned with the “Improve” and “Monitor” categories. Lastly, board members and the audit committee should receive information about the “Improve” category because they have the least time and attention to give to the risks, and instead need updates on the most critical risks.
DLA Piper also provides an equation for pairing with your risk data so you can calculate where risks fall within the matrix: [Probability * (Severity + Velocity) = Risk]. There’s some subjectivity required in order to assign points to the risks, but overall the model helps to develop a way to manage enterprise risks holistically.
To maintain your enterprise risk management strategy, we recommend the following, as suggested by DLA Piper:
- Conducting quarterly interviews of relevant stakeholders, such as HR, IT, legal, internal audit, etc., to determine what they are seeing as the top risks
- Researching externally for risks other organizations are noting, such as at conferences or in white papers
- Evaluating whether new risks affecting part of the enterprise warrants testing across the broader enterprise
- Automating as many workflows as possible to reduce the amount of manual work your team spends managing risks
The Value of Enterprise Risk Management Software

The right risk management software can help alleviate some of the stressors of enterprise risk management by giving your company a platform to simplify tasks, including evidence collection, controls monitoring, reporting and dashboarding, managing risks, and collaborating with relevant stakeholders. It can also help remove human error in the form of automation.
Automate Evidence Collection
Enterprises may find benefits in automating their evidence collection. From connecting the many systems they need to monitor to eliminating human error, automation allows for smoother management of evidence. Rather than repeatedly asking a colleague for a screenshot or proof of a process, an ideal enterprise risk management platform will have built-in reminders that help manage evidence collection. It will also integrate into all of the relevant tools you use daily for evidence management and allow you to reuse evidence across multiple controls.
Continuous Controls Monitoring
Continuous controls monitoring is defined as applying technology to allow continuous, automated monitoring of controls to validate the effectiveness of controls designed to mitigate risk, including maintaining an active cyber defense posture and ensuring business continuity and regulatory compliance.
Continuous controls monitoring means that your controls will be monitored at all times, alerting you when there’s a problem or a requirement has expired. An ideal enterprise risk management software helps you monitor hundreds of controls, with the ability to drill down into specifics when needed. No more spreadsheets are needed (unless you want them); store evidence for your controls all in one place.
Reports and Dashboards
Modern enterprise risk management software will have rich reporting capabilities, allowing you to immediately see your risk posture and know where your organization stands. It will have custom analytics, so you can break down reports to show what you care about — and support building the right reports and dashboards.
With dashboards, CISOs and board members can quickly understand your risk posture by looking at a single pane of glass without deep-diving into reports to find what they’re looking for. Better dashboarding means easier communication with leadership and the board using the data that actually matters to them, thus making your work easier.
Risk Register
The ideal enterprise risk management software should also have a risk register, where you can track and monitor all of your risks in one place. It should also provide a matrix for you to understand what and where your most critical risks are located.
Collaboration Tools
Enterprise risk management platforms should have rich collaboration tools that allow you to collaborate both with internal and external stakeholders. These tools should also provide the ability to delegate tasks to help monitor and remediate risks.
Building Your Enterprise Risk Management Strategy Doesn’t Have to Be Scary
Risk can make even the most seasoned professionals uncomfortable. It’s a tough topic to delve into because it relies on so many uncertainties and different aspects of a business and its operations. But, enterprise risk management strategy doesn’t have to be scary. Handling it with transparency, clear communication, and software can help unlock easier, more tolerable enterprise risk management methods. With a solution like Hyperproof, you can automate evidence collection, monitor your risk register, store and reuse evidence, continuously monitor your controls, collaborate with internal and external stakeholders, and generate beautiful, rich reporting and dashboards. Enterprise risk management has never been easier.
Learn more about how Hyperproof can support your enterprise risk management strategy.
The post The Ultimate Guide to Enterprise Risk Management Strategy appeared first on Hyperproof.
*** This is a Security Bloggers Network syndicated blog from Hyperproof authored by Kayne McGladrey. Read the original post at: https://hyperproof.io/resource/the-ultimate-guide-to-enterprise-risk-management/

