Analyzing CISA Known Exploited Vulnerabilities with Business Context
What is CISA Directive BOD 22-01?
In November 2021, the US Cybersecurity and Infrastructure Security Agency (CISA), an agency of the United States Department of Homeland Security (DHS), issued a new binding operational directive, BOD 22-01. The directive, titled “Reducing the Significant Risk of Known Exploited Vulnerabilities”, encourages federal agencies and public and private sector organizations to improve their vulnerability management practices and dramatically reduce their exposure to cyberattacks using a new strategy.
What problem is being addressed?
At the core of the BOD 22-01 directive is a way of dealing with cybersecurity’s proverbial ‘problem of plenty’. To understand it better, let’s look at some hard facts. The National Vulnerability Database (NVD) is the U.S. government repository of standards based vulnerability management data. It applies a standard-based approach to categorizing and classifying vulnerabilities which helps enable automation of vulnerability management, security measurement, and compliance. The NVD currently includes more than 195,000 Common Vulnerabilities and Exposures (CVEs), and is constantly growing (with over 18,500 new CVEs in 2022 so far). Each vulnerability is scored based on several factors, including ease of exploitation, potential scope and impact. The resultant score is known as Common Vulnerability Scoring System (CVSS).
However, there is a limitation in the CVSS scoring system. The CVSS base score does not account for whether the vulnerability is actually being used to attack systems. The experts at CISA have observed that attackers do not rely only on critical vulnerabilities to achieve their goals; some of the most widespread and devastating attacks have exploited vulnerabilities with low ratings. For example, through a methodology known as “chaining,” attackers have used lower score vulnerabilities to first gain a foothold, then exploit additional vulnerabilities to escalate privilege on an incremental basis.
At the opposite end of the spectrum, many vulnerabilities classified as critical are highly complex and have never been seen exploited in the wild. In fact, as is quite evident from the below data referenced from CISA website, most vulnerabilities are never exploited:
- Less than 4% of the total number of CVEs have been publicly exploited.
Attackers are generally very discriminating regarding which specific weaknesses to focus on.
Another important observation is that timing matters. Of the 4% of the CVEs that are known to have been exploited:
- 2% are being used on day 0 of disclosure;
- 50% within 2 days;
- and 75% within 28 days.
It’s clear that threat actors can be extremely quick to exploit new vulnerabilities.
As a result, security teams are in a constant race against time. They need to take care of the rapidly growing list of new detections (since timing matters). Yet, they still need to find time to fix long-pending vulnerabilities, including lower-scoring vulnerabilities that remain susceptible to popular attacks.
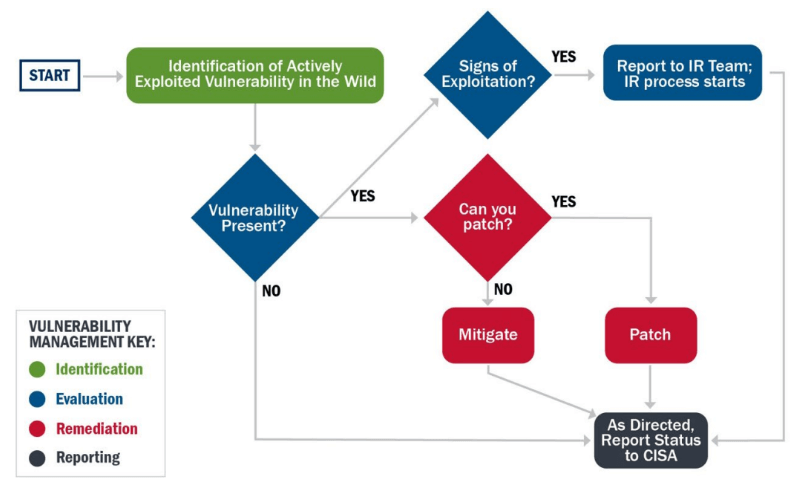
[Source: CISA Cybersecurity Incident & Vulnerability Response Playbooks]
What recommendations did CISA have to deal with these challenges?
CISA’s new strategy centers around prioritizing the remediation of vulnerabilities with known exploits that malicious threat actors are actively targeting.
To this end, the CISA has published a living catalog of known exploited vulnerabilities (KEV) that may represent significant risk for organizations. As of Oct 20 2022, the CISA KEV catalog stands at 839 vulnerabilities. The list expands each month. The directive establishes a more aggressive turnaround time for government agencies to remediate each CVE.
As a CISO or vulnerability management leader, your teams are likely already evaluating how CISA KEV intelligence could help to optimize their vulnerability management operations.
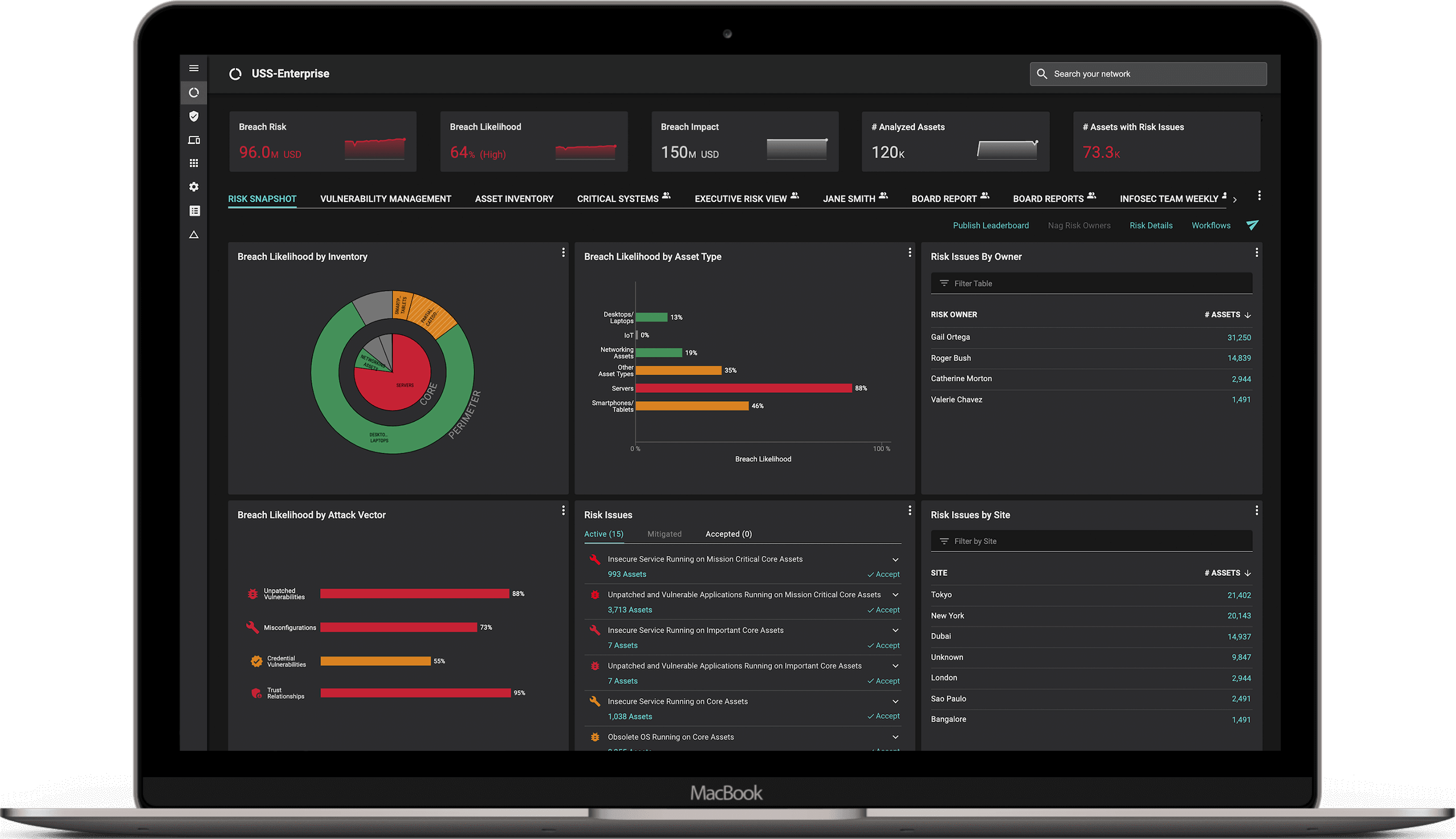
Balbix can help operationalize CISA KEV
1. Balbix’s risk-based prioritization approach automatically incorporates CISA KEV intelligence
Balbix already prioritizes vulnerabilities according to risk to help you avoid needless busy work fixing low priority issues. Balbix models five risk factors: vulnerability severity, threat level, business criticality, exposure/usage and the risk-negating effect of compensating controls. Balbix now also factors in the intelligence from the CISA KEV list as part of its determination of threat level.
2. Balbix uses CISA Known Exploited Vulnerability tags
To help you quickly identify CISA Known Exploited Vulnerabilities, Balbix now includes a tag for ‘CISA Known Exploit’. You might be wondering ‘how long Balbix takes to tag CISA KEVs?’. Balbix recognizes that when it comes to vulnerability response – speed is of essence. Balbix detects and tags the latest CISA KEVs in customer environments within a few hours of their public release by CISA.
Your team can then use Balbix’s advanced search capabilities to easily locate assets containing a CISA KEV-tagged vulnerability (filtering by tag and due date). Search results are nearly-instant, even across massive environments.
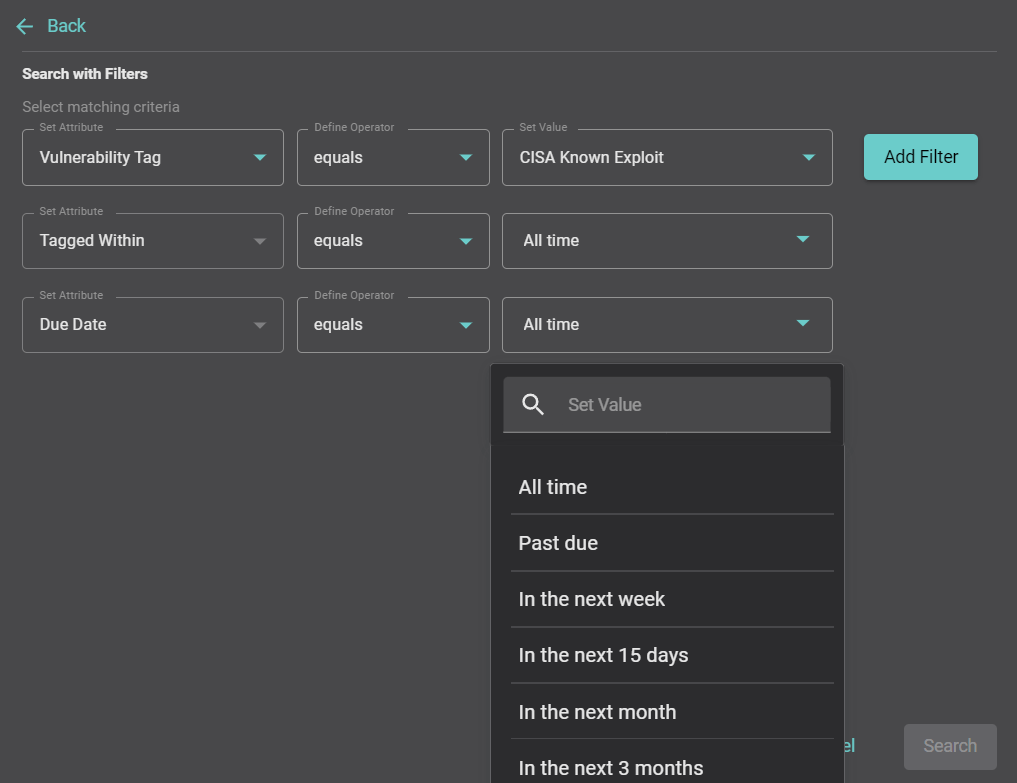
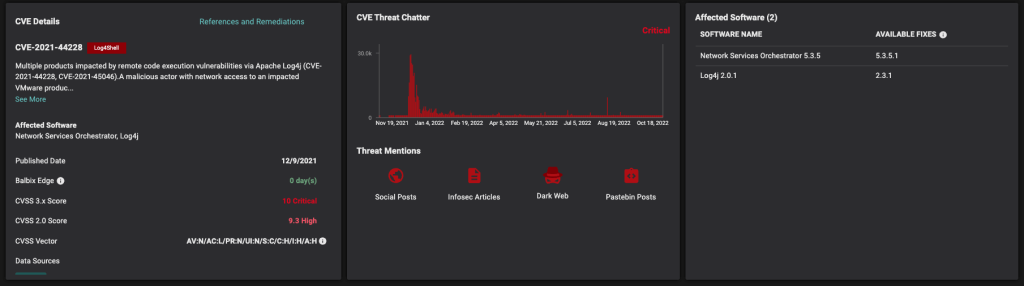
Balbix also provides additional detailed context for each CISA KEV-tagged vulnerability, including: affected software, CVSS scores, threat chatter level and threat mentions.
In addition to finding CISA KEV-tagged vulnerabilities by asset, your team can search for CISA KEV-tagged vulnerabilities amongst a list of CVEs, for example by filtering a list of CVEs with critical severity.
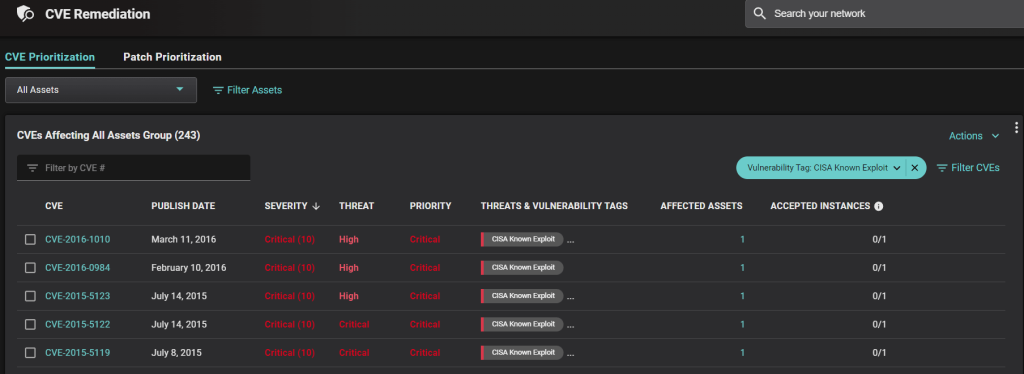
On a related note, in addition to the CISA KEV vulnerability tag, Balbix also supports the following tags:
- Exploit Kit Available: Exploit kit or proof of concept code is known to be publicly available for exploit of this vulnerability.
- Known Exploit: Vulnerability is known to have been exploited in the wild, per multiple threat intelligence sources.
- Malware Linked: Vulnerability is known to be utilized by one or more malware variants.
- Ransomware Linked: Vulnerability is known to be utilized by one or more ransomware variants or threat actors deploying ransomware.
3. Balbix adds business context to enable dollar-based risk quantification
Balbix uniquely adds business context to assets, including assets’ purpose (e.g., supporting a mission-critical customer-facing application). We do this by analyzing and correlating over 400 asset attributes, automatically estimating breach impact per asset, and incorporating expert input related to breach impact. The enriched asset and risk information is then incorporated into the Balbix fact-based risk model, and breach risk is estimated based on the likelihood and impact of a breach risk on a per asset and per vulnerability basis. Risk scores are presented in dollars to further help your team prioritize the remediation of CISA Known Exploited Vulnerabilities and other exposures.
Take full advantage of CISA KEV intelligence and start your own journey to security posture automation by scheduling a 30-minute demo with Balbix.
*** This is a Security Bloggers Network syndicated blog from Blog – Balbix authored by Chris Griffith. Read the original post at: https://www.balbix.com/blog/analyzing-cisa-known-exploited-vulnerabilities-with-business-context/

