Announcing Cybersecurity Posture Automation for GCP and Multi-Cloud Environments
The cover of Verizon’s Data Breach Investigation Report 2022 depicts an empty, and unguarded, server room, an image eerily similar to the cover of the inaugural edition. This is the stark reality of the state of cybersecurity: despite all the advances in technology over the past 15 years, assets and data remain vulnerable to cyber attacks.
In recent years, cloud adoption has been the most significant aspect of digital transformation contributing to organizations’ exposure. The cloud has become almost an inseparable part of our work lives. A trend, accelerated by the tailwinds of Covid-19 and the resultant culture of hybrid work.
Today, to help security teams better protect the cloud, Balbix is announcing our support for Google Cloud Platform (GCP). Security teams can use Balbix to easily quantify, prioritize and mitigate risks in their Google Cloud environments. Balbix has also extended its Cyber Asset Attack Surface Management (CAASM) solution to support multi-cloud environments that span both GCP and Amazon Web Services (AWS).
Support for GCP
With the newly announced support for GCP, you can continuously monitor popular GCP cloud services including: Compute Engine, Cloud Storage, Cloud SQL, Google Kubernetes Engine (GKE) Cluster & Deployments, Cloud Functions, Cloud Key Management Service (KMS), Pub/Sub and Secret Manager.
By using Balbix, you can also integrate asset data from Google Cloud with data from your existing IT and security tools to map over 400 system-level and risk-related attributes. That includes quantifying cyber risk in terms of breach impact in dollars (or other local currency) and breach likelihood (in %). In addition, you can align Google Cloud assets to your business organization by business unit, geography, site or business owner.
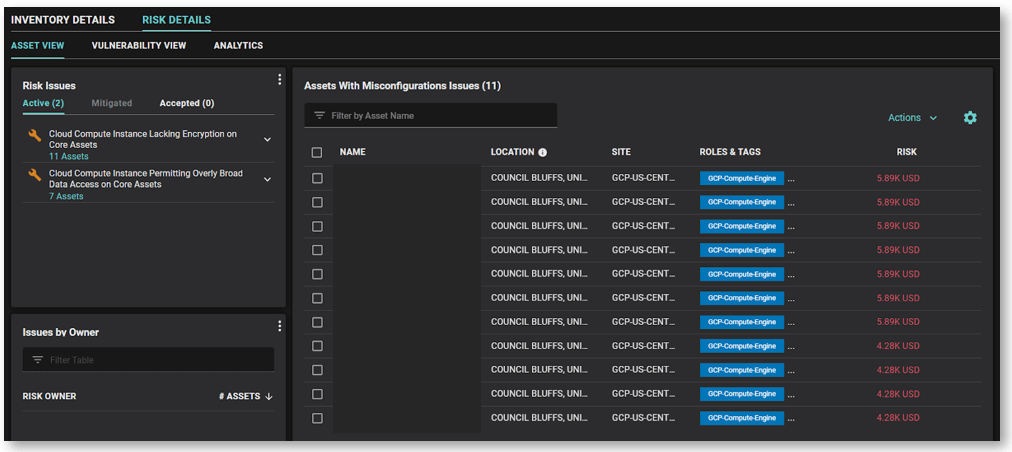
Balbix also provides you with a prioritized list of vulnerabilities in your Google Cloud environment. Vulnerabilities are prioritized for each asset, and for your GCP assets collectively. Balbix identifies exposure to common attack vectors, notably misconfigurations – the most exploited attack vector for the cloud – including issues with data encryption and overly permissioned instances.
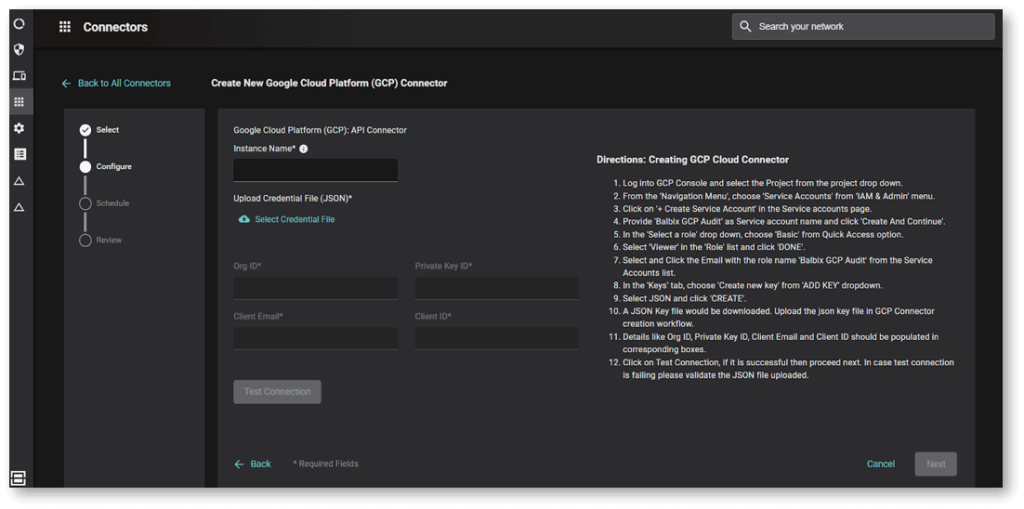
To see asset and misconfiguration data, you can easily connect Balbix and GCP using our API connector and start ingesting data into Balbix within minutes using a wizard-driven configuration process.
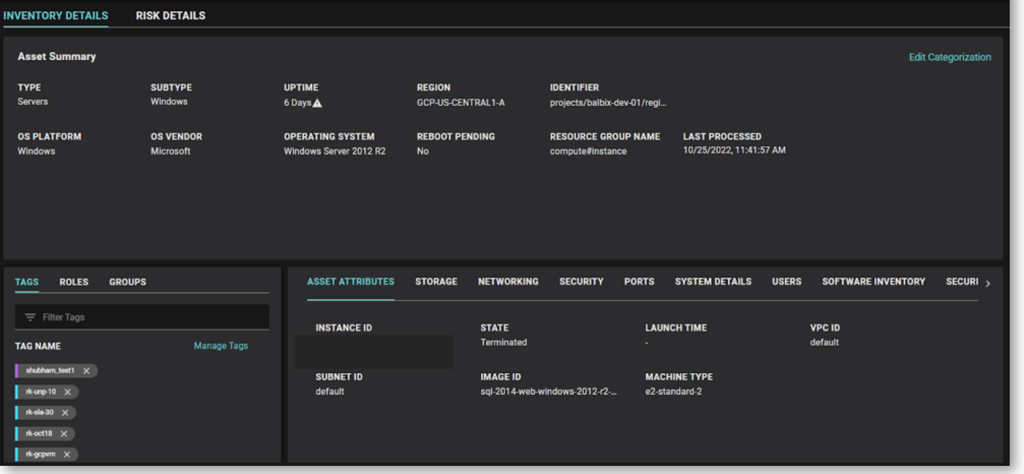
Visibility into other types of vulnerabilities – such as unpatched software vulnerabilities, weak credentials and trust issues – is provided by optional Balbix sensors. Balbix sensors also capture system details such as network, storage, open ports, system details, users, software inventory, the software bill of materials (SBOM) and any existing (or missing) security controls for virtual machines.
The Connector for GCP provides resource information for other resource types. Data from the Connector for GCP and optional sensors is unified and correlated by Balbix.
Cyber Asset Attack Surface Management for Multi-Cloud Environments
Cybersecurity Insiders reports that 76% of organizations are now multi-cloud, i.e. using two or more cloud providers, compared to just 62% last year. Multi-cloud deployments have allowed organizations to work more efficiently and scale more easily but in doing so they have also added a new dimension of complexity from a cybersecurity standpoint. For example, Cybersecurity Insiders also report that organizations have inadequate visibility of their asset inventory and their security. According to their survey, 58 percent of organizations are aware of fewer than 75 percent of the assets on their network.
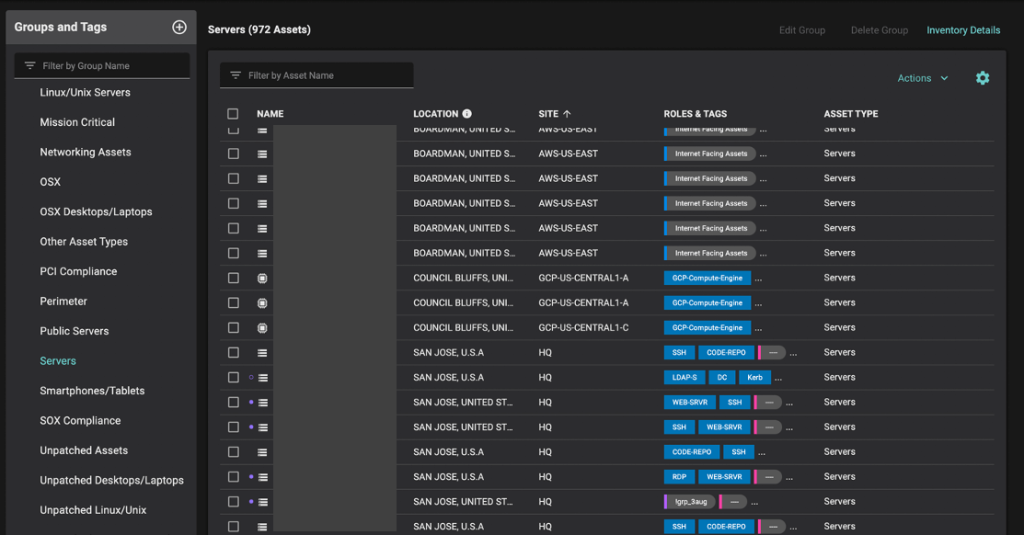
With the release of our support for GCP, Balbix’s Cyber Asset Attack Surface Management (CAASM) can help you improve your visibility of multi-cloud environments (GCP and AWS). Our CAASM solution also extends to on-prem environments. You can group and analyze those assets by business unit, by asset type or geographical location. The image below shows a server group with servers in GCP, AWS and on-premises at the organization’s HQ.
Security posture automation
Balbix provides more than just visibility. Unlike other vendors, Balbix combines CAASM with Risk-Based Vulnerability Management (RBVM) and Cyber Risk Quantification (CRQ) solutions.
With RBVM, you can prioritize and mitigate unseen risks across multi-cloud and hybrid environments, including risks such as unpatched software vulnerabilities, weak credentials, missing security controls, poor encryption, trust issues and cloud infrastructure misconfigurations.
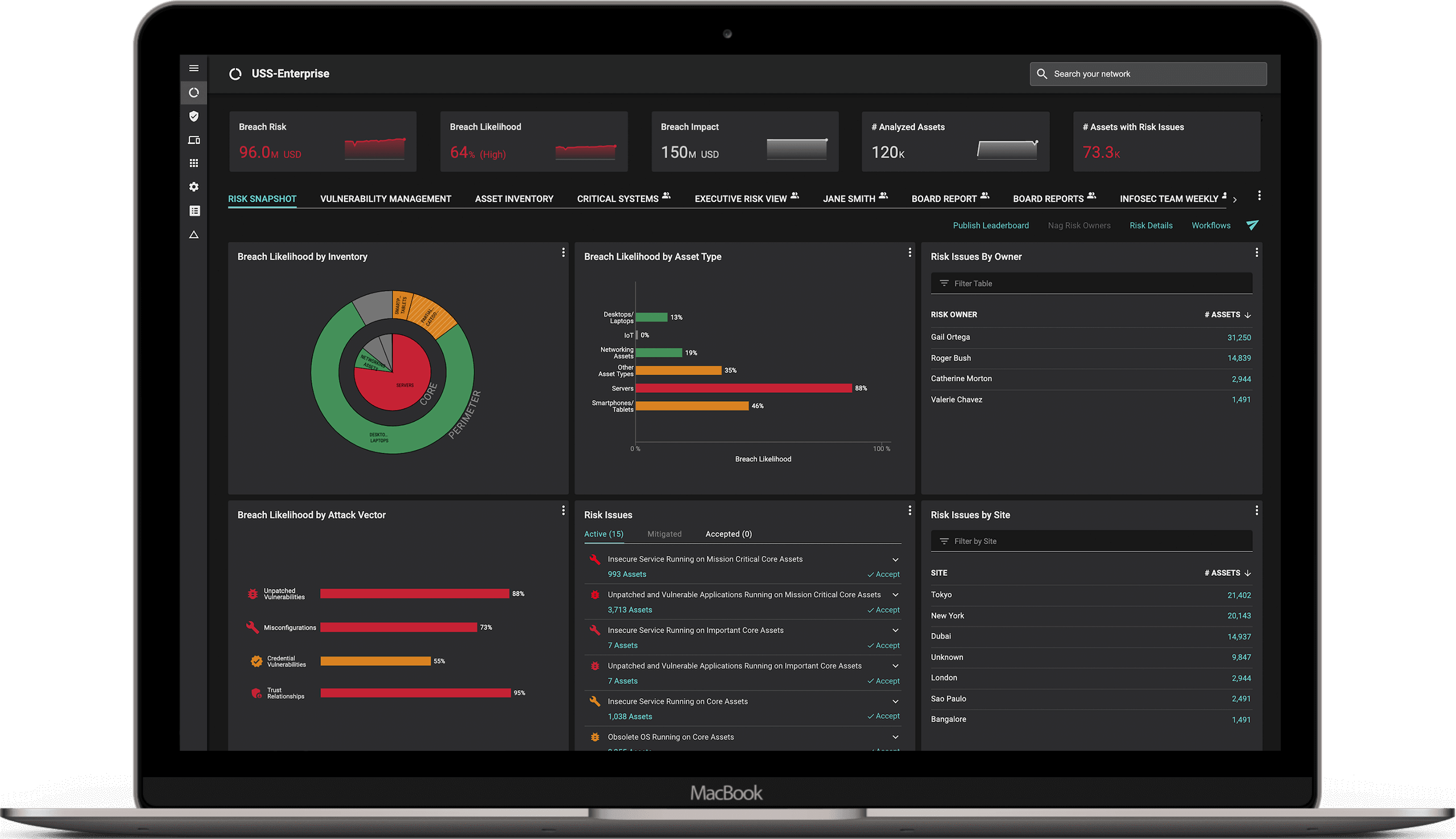
As you can see in the image above, with Balbix CRQ, you can also report on the overall likelihood and impact of a breach. Moreover, you can calculate cyber-risk in dollars (or other local currencies) to report on cyber risk to the board, to demonstrate the ROI of your security investments and to help you negotiate favorable cyber insurance insurance terms.
*** This is a Security Bloggers Network syndicated blog from Blog – Balbix authored by Chris Griffith. Read the original post at: https://www.balbix.com/blog/announcing-cybersecurity-posture-automation-for-gcp-and-multi-cloud-environments/

