3 Ways Balbix can help operationalize CISA BOD 23-01


March 31, 2023
Take the Complexity Out of CISA Directive BOD 23-01 Compliance with Balbix’s Unified Approach
Picture this: you’re a cybersecurity expert working for a US federal civilian agency. You’ve just heard about a new directive from the Cybersecurity and Infrastructure Security Agency (CISA) that requires your agency to improve asset visibility and vulnerability detection on federal networks. It’s a big ask, but luckily, Balbix can help.
Let’s begin with a quick review of the basics.
What is CISA Directive BOD 23-01?
In October 2022, the US Cybersecurity and Infrastructure Security Agency (CISA), which is a part of the United States Department of Homeland Security (DHS), issued a new directive called BOD 23-01. This directive, titled “Improving Asset Visibility and Vulnerability Detection on Federal Networks”, requires that all US federal civilian agencies take measurable steps to enhance their ability to detect vulnerabilities and gain better visibility into their agency’s assets. The ultimate goal of this directive is to improve their overall operational visibility into agency assets for a successful cybersecurity program.
What is in-scope for CISA Directive BOD 23-01?
Binding Operational Directives (BODs) are a type of directive that are periodically issued by the CISA in order to keep pace with the rapidly evolving cybersecurity paradigm. BODs require federal civilian agencies to take specific actions to improve their cybersecurity posture with the goal of providing a uniform and consistent approach to improving the cybersecurity of federal networks. Here is the summary of what the BOD 23-01 expects all the Federal Civilian Executive Branch (FCEB) agencies (or any entity acting on behalf of an FCEB agency) to comply with by Apr 3, 2023.
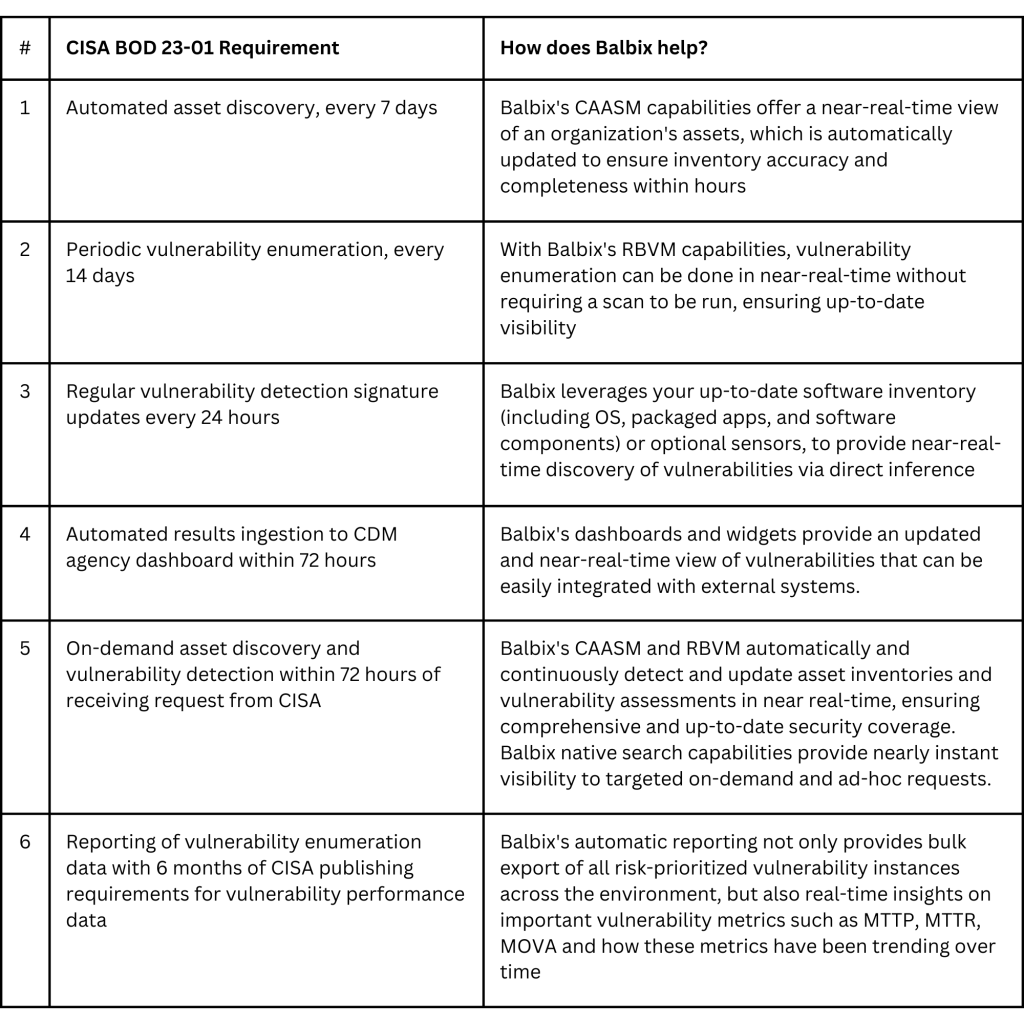
- Automated asset discovery: Perform automated asset discovery every 7 days.
- Periodic vulnerability enumeration: Initiate vulnerability enumeration across all discovered assets, including managed endpoints (e.g., servers, workstations, desktops, laptops), managed network devices (e.g., routers, switches, firewalls), mobile devices (e.g., iOS and Android) , discovered nomadic/roaming devices (e.g., laptops), every 14 days. All vulnerability enumeration must be conducted with privileged credentials.
- Regular signature updates: All vulnerability detection signatures used must be updated at an interval no greater than 24 hours from the last vendor-released signature update.
- Automated results ingestion: Initiate automated ingestion of detected vulnerabilities into the Continuous Diagnostics and Mitigation (CDM) Agency Dashboard within 72 hours of discovery completion.
- On-demand asset discovery and vulnerability detection: Develop and maintain the operational capability to initiate on-demand asset discovery and vulnerability enumeration to identify specific assets or subsets of vulnerabilities within 72 hours of receiving a request from CISA and provide the available results to CISA within 7 days of request.
- Reporting of vulnerability enumeration data: Within 6 months of CISA publishing requirements for vulnerability enumeration performance data, all FCEB agencies are required to initiate the collection and reporting of vulnerability enumeration performance data, as relevant to this directive, to the CDM Dashboard.
It’s about Asset visibility and Vulnerability enumeration
To keep things simple, the main emphasis of BOD 23-01 is on two crucial activities that play a vital role in enhancing operational visibility for a cybersecurity program to succeed: identifying assets and enumerating vulnerabilities. As described in the directive-
Asset discovery is a building block of operational visibility. It involves identifying the network addressable IP assets on an organization’s network and determining their associated hosts. This process is non-intrusive and typically does not require any special logical access privileges.
Vulnerability enumeration is the process of identifying and reporting suspected vulnerabilities on the organization’s assets. It involves detecting host attributes, such as operating systems, applications, and open ports, as well as identifying outdated software versions, missing updates, and misconfigurations. By matching the host attributes with information on known vulnerabilities, vulnerability enumeration can validate compliance with or deviations from security policies. However, understanding an asset’s vulnerability posture requires appropriate privileges, which can be obtained through credentialed network-based scans or a client installed on the host endpoint.
Balbix can help operationalize CISA BOD 23-01
Balbix uses AI and automation to reinvent how the world’s leading organizations reduce breach risk. Balbix’s unified asset and risk model provides security teams with comprehensive cybersecurity posture automation driven by Cyber Asset Attack Surface Management (CAASM), Risk-Based Vulnerability Management (RBVM) and Cyber Risk Quantification (CRQ) use cases.
Here are 3 ways Balbix can help operationalize CISA BOD 23-01-
1. Balbix’s CAASM Capabilities Enable Continuous and Up-To-Date Asset Discovery
Balbix Cyber Asset Attack Surface Management (CAASM) provides organizations with a real-time, up-to-date view of their assets and clearly lays out the attack surface. It enables security teams to improve basic security hygiene by ensuring security controls, security posture, and asset exposure are understood and remediated. Balbix’s CAASM capabilities help meet and exceed CISA BOD 23-01’s automated and on-demand asset discovery options.
a. Continuous and Unified Asset Discovery: Balbix continuously ingests data from your IT, cloud, cybersecurity, GRC and in-house tools to create a unified view of all your assets. This includes devices, apps, and services; managed or unmanaged (Shadow IT); on-prem and cloud; fixed and mobile; and IoT/OT.
b. Automatic Categorization of the Assets: During the asset discovery process, conflicting and duplicate data is cleaned, correlated and merged automatically, and coverage gaps are identified. Assets are automatically categorized by type and role. All this is done without the need to run a scan!
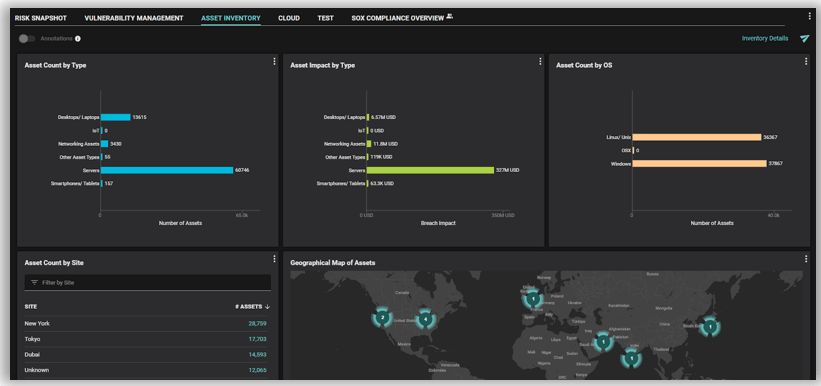
c. Granular Asset Attributes Tracking: Balbix uniquely adds business context to assets, including an asset’s purpose (e.g., supporting a mission-critical customer-facing application). We do this by analyzing and correlating over 450+ asset attributes, including general asset information, and information about its network, storage, open ports, system details, users, software inventory, and any existing (or missing) security controls, as well as by correlating contextual data and tags from relevant tools, such as a CMDB. Customizable dashboards with search capabilities allow you to see your assets in the context of the business and organization.
d. Software Bill of Materials: Balbix provides a near real-time inventory of the runtime software bill of materials (SBOM). By accessing the SBOM view, security teams know exactly which software components (and versions) are deployed in the environment, where they were installed, and the full path and version of the components. This includes comprehensive visibility of software components (including open-source and third-party packages).
e. Dynamically Track and Trend Groups of Assets: With Dynamic Grouping of Assets, you can easily define custom groups based on a range of asset attributes. This means that you can closely monitor your most critical assets, making it easier to track and stay ahead of any potential threats.
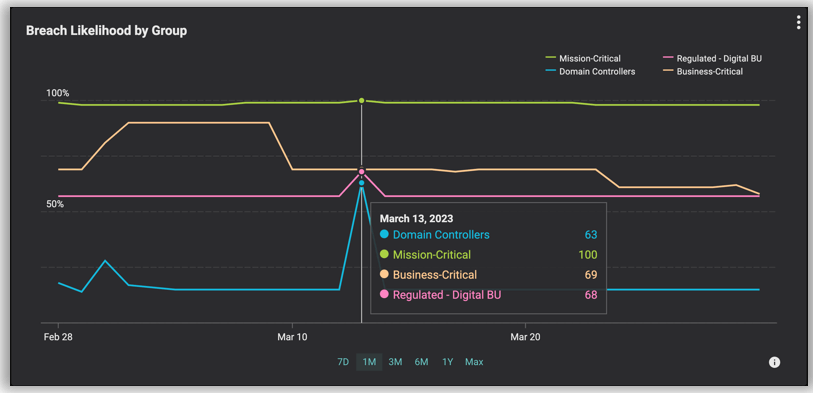
2. Balbix’s RBVM capabilities enable Near-Real-Time Vulnerability Enumeration
Balbix’s Risk Based Vulnerability Management (RBVM) capabilities help you prioritize and mitigate risky vulnerabilities before they can be exploited and dramatically improve your security posture.
a. Unified Vulnerability Visibility across all sources: Balbix consolidates all vulnerabilities into a single unified model by continually ingesting findings, including CVEs and misconfigurations, from your various vulnerability assessment tools, including IT infrastructure, IoT/OT, web apps, and cloud.
b. Near Real-Time Vulnerability Inference: Balbix leverages your up-to-date software inventory (including operating system, packaged apps, and software components) or optional sensors, to provide near-real-time discovery of vulnerabilities via direct inference, with no additional scans required. Balbix vulnerability inference dramatically increases detection speed and coverage – enabling high-accuracy vulnerability detection on assets not covered by your existing assessment tools. Balbix inferred vulnerabilities are deduplicated and corroborated with those generated from 3rd party tools, ensuring a comprehensive and up-to-date view.
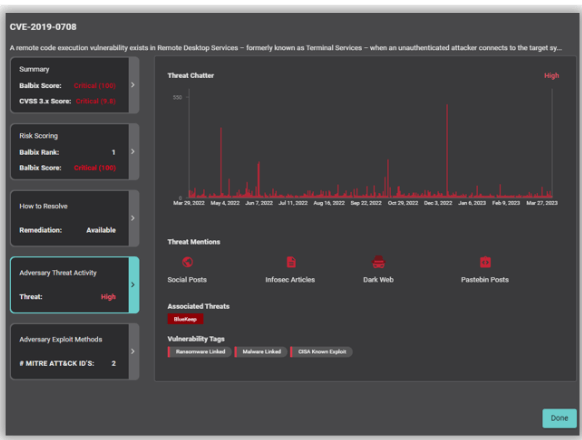
c. Software Component Vulnerability Detection: In addition to providing real-time visibility into the SBOM, including full dependency tree, Balbix also enables you to identify the most challenging modern vulnerabilities such as Log4j and Spring4Shell, which are difficult to detect accurately using traditional methods. The process of identifying software component vulnerabilities with Balbix is straightforward. Simply search for unpatched or vulnerable software among the assets in your environment.
d. True Risk-Based Prioritization: Balbix’s risk-based prioritization is built on a comprehensive five-pronged risk equation that includes vulnerability severity, threat level, business criticality, exposure, and the risk-negating effect of compensating security controls. This results in highly accurate prioritization that aligns with your business needs, helping you avoid unnecessary work fixing low-priority issues.
e. MITRE ATT&CK Framework Mapping for Each Vulnerability: Balbix automatically maps all vulnerabilities and deployed endpoint security controls to the MITRE ATT&CK framework, enhancing breach likelihood accuracy and providing a more precise risk calculation and prioritization. This enables security teams to better prioritize which vulnerabilities to address first, provides a more accurate assessment of risk, and facilitates the calculation of the return on investment (ROI) of existing or potential security tools.
3. Balbix’s Comprehensive Dashboards and Reports Gamify the Process of Risk Reduction
With Balbix, you can answer a nearly unlimited number of questions that come up as your vulnerability management teams go about their daily work. Balbix search allows you to query using the vocabulary of cybersecurity, IT, business tags/names, and cyber risk, e.g., “Which domain controllers in EMEA supporting our Retail BU are non-compliant to patch SLAs?”
Balbix’s dashboards and purpose-built widgets facilitate efficient risk-based vulnerability management. Think of Balbix’s dashboards as a distributed workbench for your team or organization that enables real-time monitoring, analysis, and collaboration. Executive and operational dashboards and reports can be shared with the key stakeholders involved, effectively gamifying the process of overall cyber risk reduction.
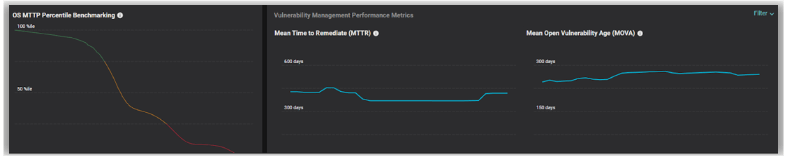
For instance, Balbix provides automatic reporting on a range of key metrics, including mean-time-to-patch (MTTP), mean-time-to-remediate (MTTR), as well as mean-open-vulnerability age (MOVA). Balbix provides percentile benchmarking against a broad range of enterprise peers, key for absolute gauges of performance as well as tuning organizational SLA policies.
In summary
Balbix offers a comprehensive solution to meet the CISA BOD 23-01 requirements for asset discovery and vulnerability enumeration. By leveraging the power of CAASM, RBVM, and Dashboard and Reporting capabilities, organizations can gain complete visibility into their assets and vulnerabilities, identify and prioritize risks, and take proactive steps to mitigate them.
Start your own journey to security posture automation by scheduling a 30-minute demo with Balbix.
*** This is a Security Bloggers Network syndicated blog from Blog – Balbix authored by Chris Griffith. Read the original post at: https://www.balbix.com/blog/3-ways-balbix-can-help-operationalize-cisa-bod-23-01/

